"Data Security + Risk Management in IT consumerization is inevitable, as a variety of laptops, smartphones, and tablets, including those enterprise provisioned and individually owned endpoints devices, enter the environment." - Lightedways Tech
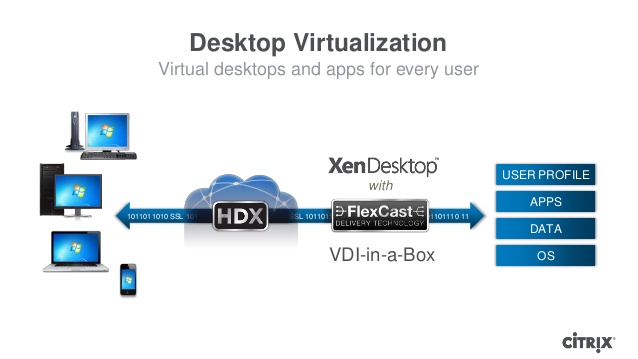 |
Photo: https://www.slideshare.net
|
By the way initiatives of BYOD (Bring-your-own-Device), flexwork, and mobility increased in popularity, IT risk profile has significantly changed. The ways of collaborating and working environments now need new strategies to managing risk leading organizations to weigh things entirely in new perspectives: giving its people the flexibility needed for most favorable business efficiency while guaranteeing the safety measures and compliance needed by the business in its operation.
Operating at its maximum competitiveness and performances, organizations need data security analysts to access organization’s resources in more locations and in many more ways than in the past. But surely that is not some easy tasks primarily because the resulting proliferation of work locations, access methods, and types of workers has broken off traditional security policies to the brink.
Operating at its maximum competitiveness and performances, organizations need data security analysts to access organization’s resources in more locations and in many more ways than in the past. But surely that is not some easy tasks primarily because the resulting proliferation of work locations, access methods, and types of workers has broken off traditional security policies to the brink.
IT consumerization is inevitable, as a variety of laptops, smartphones, and tablets, including those enterprise provisioned and individually owned endpoints devices, enter the environment. The multiplicity of devices has led to excessive and superfluous complexity and to the same extent lots of combinations of apps, configurations, and the operating system has wiped out the consistency model of the corporate-managed device.
Though technologies such as access control, antivirus, firewalls and perimeter monitoring remain as important as it used to be, these are ever more being circumvented because these days adept attackers directly target apps, data, and devices. Therefore, what is needed today is a security layer that builds possibilities to further manage threats effectively.
Desktop virtualization provides the most suited security layer, bestowing organizations the complete freedom to adopt business initiatives including BYOD, flexwork, and mobility and deploy resources and personnel whenever and wherever they’re maybe needed.
Simultaneously, desktop virtualization, supplemented by enterprise mobility management and secure file sharing, helps fortify data security and compliance across apps, data, and devices in support of business and the IT’s main concern. The use of app and desktop virtualization in strengthening data security includes;
> The rising challenges of maintaining data security in today’s ever-evolving enterprise environment
> App and desktop virtualization key advantages as an integrally more secure computing infrastructure
> Top benefits of using app and desktop virtualization in strengthening information security
Increasing intricacy places organizations in jeopardy
Even though achieving effective data security is key, maintaining protection at a high level is an increasingly continuous challenge. Adding to the fact that flexwork, mobility and IT consumerization including BYOD and cloud computing mean involving more people, including mobile users, teleworkers, outsourcing providers, partners and all other contractors are accessing organizations apps and data from more locations or more endpoints devices in more ways than ever before. Accordingly, business data is now everywhere, precisely at employee’s homes, on business-issued or individually-owned endpoints devices, in public and private clouds, at partner organizations, on the business floor, and much more. It is endless!
Increasingly, data security has become a critical concern for all organizations. These days’ threats are more powerful than ever before, stretching from infecting the corporate networks by traditional malware to directed hacking, the sophistication of phishing attacks and out-and-out tampering with or stealing of assets and intellectual property rights, not to mention of people simply forgetting their smartphone or tablet somewhere.
Security occurrences are also disrupting the continuity of business functions, which cannot return to normal operations until such time the breach has been diagnosed and stopped and damage have been evaluated and mended. If securing traditional PC across a broad landscape is not challenging enough, IT must now also account for a multitude of devices, including laptops, smartphones, and tablets, especially when BOYD strategies are becoming more extensive and practice. Organizations must recognize that these devices, in addition to its operating system and apps, must be kept current with the latest technologies and using traditional security methodologies makes this attempt almost impossible.
On the other side of the coin, IT must also uphold commitments and maintain compliance with;
> countless nitty-gritty of security requirements demystified in contractual collaborations with consumers and partners,
> laws, policies and regulations on data privacy and compliance that differ throughout the geographies and industries,
> the organization’s very own best practices for compliance, data security, privacy, and retention policies specifically designed to safeguard its fundamental interests.
But even with the myriad of data security policy and technology available within grasp, it is not surprising that many in IT organizations feel like they’re rapidly falling behind and slowly swallowed in a quicksand of uncertainty. Even though they spend more money on security excessively, they failed miserably in addressing the innate insufficiency of legacy security policies to protect today’s more convoluted computing thermospheric environments.
But, how can IT reclaim the control over data and lower the growing threats to the organization? The easiest approach to this question is to block access and compel everybody to work within the organization’s LAN and on organization-standard devices, but this would inflict deplorable limitations on the organization’s agility and productivity, not to even mention employee discontent against too restrictive environments. In the end, IT is supposed to be helping people to get business done, not to hinder their productivity.
 |
VDI/VAP – Virtual Desktop Infrastructure/App | Source: http://www.trend.ro/vdivap-virtual-desktop-infrastructureapp/
|
App and Desktop Virtualization = Data Security + Risk management
App and desktop virtualization provides organizations and improve the system to safeguard their data and to manage risk. The basis of app and desktop virtualization is the IT centralization of resources in the data center which is an integrally protected architecture that makes it far easier to equally control both information and access. Centrally administered virtualized Windows apps and desktops are provided on demand as a service to any device, presenting an experience that acts, feels, and looks very similar to working on a traditional PC.
A well-designed, well-made app and desktop virtualization solution presents very important advantages and benefits over time-honored security models, to wit;
● Centralized Resources-
Enterprise Windows apps and allied data are managed and safeguarded in the data center and can be securely accessed from any locations, instead of residing in the endpoint devices of everyone in the expanded organization. The resulting model will highly and vastly lessen business risk. IT gets complete control and visibility over the centrally managed Windows apps and desktops, and consequently, IT can simply delineate and put into effect strategies vis-à-vis which resources individual users or teams can access, and in any case, they can install and configure apps themselves. Access to Windows app and desktop can be switched on and off instantaneously, as necessary to accommodate new, departing and transferring employees and business continuity situations where selected people need to take up bigger responsibility.
● Multiple-level strategy-based access control –
Preconfigured strategies can be leveraged by IT to determine the applicable level of user access to Windows apps to wherever they reside - in the data center, in a public or private cloud or even those downloaded to a local device intended for offline use, where encryption, complete isolation, and stringent control over save and copy functionality and marginal usage prevent data from going off course. Strategy-based access control supports multiple-level security systems by allowing IT to deliver the ideal level of access based on the user’s present profile, device, location, and network. For example, a user can be permitted to access a single set of resources from the office, a subsection of those resources from a personal computer at home and an analogous subsection from a leased device or while linked via a public hotspot. Additionally, in controlling which and what resources a user possibly will access, granular strategies can ascertain what activities they might perform with every app. For instance, a policy may possibly point out that when a user used an organization managed device the user could download, print or upload data, but when using an unreliable device such as a public stall or a personal tablet, the user could just simply view the data.
● Any-device accessibility –
Since virtualized Windows apps and desktops are hardware independent, IT can facilitate a secured access and collaborate with every employee, contractor, and partner from every personal or organization-owned device they decide on to use. Instead of making any distinctions between individually-owned and organization-owned devices, IT will just assess every device and user in accordance with admin-defined standards as users attempt to link up to the organization network, then grants the user the apposite level of access to every resource as specified by access control system protocols.
● Built-in data compliance –
In ensuring conformity, IT can define and implement strategies with the complete gamut of requirements the organization encounters, both internally and externally, while maintaining the agility to respond to new emerging mandates. The centralism of resources, coupled with the stringent access control is making effortless protection against data loss and ensuring a full activity logging, auditing and reporting to meet up compliance and privacy benchmarks.
One key driving force why organizations are adopting app and desktop virtualization is security. In making the app and desktop virtualization a vital component of security, IT can manage threat more effectively while providing the organization with the optimum flexibility to do whatever and wherever it needs to do.
Conclusion
Therefore, leveraging a virtualized desktop as a security stratum, organizations can ably support important primacies such as BYOD, flexwork and mobility while coping with risk more effectually. Additionally, applications and allied information are not at all strewn beyond IT’s control for they remain where they appropriately belong – in the data center – where they facilitate better business worth than ever before.

